I recommend to achieve the task via GPO. Chrave Information Technology is an IT service provider.
Click OK. Why did it take over 100 years for Britain to begin seriously colonising America? Visit Microsoft Q&A to post new questions. I know this isn't exactly what you asked, but thought it would be a good FYI that I've recently dealt with for you.
What is the Advantage of the Home Folder "Local Path", http://technet.microsoft.com/en-us/library/ee308297.aspx, http://technet.microsoft.com/en-us/library/cc179081.aspx.
Oh and Happy Sysadmin Day!Just a reminder, if you are reading the Spark!, Spice it Use DNS name resolution when a single-label domain name is used, by appending different registered DNS suffixes, if the AllowSingleLabelDnsDomain setting is not enabled.
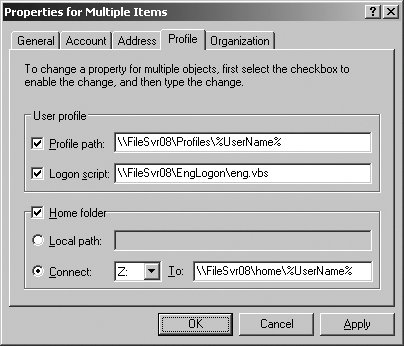 This topic has been locked by an administrator and is no longer open for commenting. Thanks for contributing an answer to Server Fault! This policy setting allows you to specify the location and root (file share or local path) of a user's home folder for a logon session. How can one check whether tax money is being effectively used by the government for improving a nation?
This topic has been locked by an administrator and is no longer open for commenting. Thanks for contributing an answer to Server Fault! This policy setting allows you to specify the location and root (file share or local path) of a user's home folder for a logon session. How can one check whether tax money is being effectively used by the government for improving a nation? For example - redirect "My Documents" but leave "My Music" local.
Hide the TPM Firmware Update recommendation. Announcing the Stacks Editor Beta release! ethics of keeping a gift card you won at a raffle at a conference your company sent you to? Click Properties, Step 10: Open Profile tab and check the home folder. If you enable this policy setting, the user's home folder is configured to the specified local or network location, creating a new folder for each user name.
Thanks Marcin, I checked and what you said is totally right, but still I didn't get it, what is the use of the "Local Path" feature ??
What is the best way to either push a GPO or use Powershell to basically populate this field in AD without having to go to each user manually? Last Updated on January 17, 2017 by FAQForge, Enabling and Restoring Recycle Bin in Active Directory Domain Services in Server 2012 R2, Use the Echo Command with Examples in Linux, Four Ways to Create a Directory with PowerShell, Find and Open Files using Windows Command Prompt. More like San Francisgo (Ep.
What am I missing? The best answers are voted up and rise to the top, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site, Learn more about Stack Overflow the company, Set user home folder to local path doesn't seem to actually set the profile location for domain or local users, Measurable and meaningful skill levels for developers, San Francisco?
By default, offline use is enabled so those folders are always available.
I'd appreciate if someone clarify to me the use of "Local Path" and how to use it?
AD. Good point. Set a default associations configuration file, Start File Explorer with ribbon minimized, Turn off Data Execution Prevention for Explorer, Turn off numerical sorting in File Explorer, Verify old and new Folder Redirection targets point to the same share before redirecting, Turn off tracking of last play time of games in the Games folder, Prevent the computer from joining a homegroup, Restrict Accelerators to those deployed through Group Policy, Bypass prompting for Clipboard access for scripts running in any process, Bypass prompting for Clipboard access for scripts running in the Internet Explorer process, Define applications and processes that can access the Clipboard without prompting, Turn off the ability to launch report site problems using a menu option, Include updated website lists from Microsoft, Turn on Internet Explorer 7 Standards Mode, Turn on Internet Explorer Standards Mode for local intranet, Use Policy List of Internet Explorer 7 sites, Prevent specifying the code download path for each computer, Prevent access to Delete Browsing History, Prevent deleting ActiveX Filtering, Tracking Protection, and Do Not Track data, Prevent deleting InPrivate Filtering data, Prevent deleting temporary Internet files, Prevent deleting websites that the user has visited, Prevent the deletion of temporary Internet files and cookies, Allow active content from CDs to run on user machines, Allow Install On Demand (except Internet Explorer), Allow Install On Demand (Internet Explorer), Allow Internet Explorer to use the HTTP2 network protocol, Allow Internet Explorer to use the SPDY/3 network protocol, Allow software to run or install even if the signature is invalid, Automatically check for Internet Explorer updates, Check for signatures on downloaded programs, Do not allow ActiveX controls to run in Protected Mode when Enhanced Protected Mode is enabled, Do not allow resetting Internet Explorer settings, Empty Temporary Internet Files folder when browser is closed, Turn off loading websites and content in the background to optimize performance, Turn off sending UTF-8 query strings for URLs, Turn off the flip ahead with page prediction feature, Turn on 64-bit tab processes when running in Enhanced Protected Mode on 64-bit versions of Windows, Allow websites to store application caches on client computers, Allow websites to store indexed databases on client computers, Set application caches expiration time limit for individual domains, Set application cache storage limits for individual domains, Set indexed database storage limits for individual domains, Set maximum application cache individual resource size, Set maximum application cache resource list size, Set maximum application caches storage limit for all domains, Set maximum indexed database storage limit for all domains, Start Internet Explorer with tabs from last browsing session, Allow active content over restricted protocols to access my computer, Allow cut, copy or paste operations from the clipboard via script, Allow drag and drop or copy and paste files, Allow loading of XAML Browser Applications, Allow only approved domains to use ActiveX controls without prompt, Allow only approved domains to use the TDC ActiveX control, Allow OpenSearch queries in File Explorer, Allow previewing and custom thumbnails of OpenSearch query results in File Explorer, Allow script-initiated windows without size or position constraints, Allow scripting of Internet Explorer WebBrowser controls, Allow VBScript to run in Internet Explorer, Allow video and animation on a webpage that uses an older media player, Allow websites to open windows without status bar or Address bar, Allow websites to prompt for information by using scripted windows, Don't run antimalware programs against ActiveX controls. After logging in for the first time with a domain or local user, a folder does get automatically created in a format of DOMAIN.user but the folder contents are empty and it looks like Windows is using a folder under C:\Users for all the contents that would typically be in a user profile folder like Documents, etc. Asking for help, clarification, or responding to other answers. Have a great day, I know I will! Busting at the edges and running towards technology as fast as we can.
What is wrong here? What happens?
Those files can roam around on any computer within the domain where user login. To continue this discussion, please ask a new question.
Turn on dynamic Content URI Rules for Windows store apps, Prevent backing up to optical media (CD/DVD), Prevent the user from running the Backup Status and Configuration program, Turn off the ability to back up data files, Turn off the ability to create a system image, Disallow locally attached storage as backup target, Allow domain users to log on using biometrics, Specify timeout for fast user switching events, Allow access to BitLocker-protected fixed data drives from earlier versions of Windows, Choose how BitLocker-protected fixed drives can be recovered, Configure use of hardware-based encryption for fixed data drives, Configure use of passwords for fixed data drives, Configure use of smart cards on fixed data drives, Deny write access to fixed drives not protected by BitLocker, Enforce drive encryption type on fixed data drives. http://technet.microsoft.com/en-us/library/cc179081.aspx. Stack Exchange network consists of 181 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn, share their knowledge, and build their careers. Configure the system to clear the TPM if it is not in a ready state.
If you choose "On the local computer," enter a local path (for example, C:\HomeFolder) in the Path box. No need to go use GPP mappings for home folders. This causes a certain amount of confusion. Define security intelligence location for VDI clients.
http://technet.microsoft.com/en-us/library/ee308297.aspx The Earth is teleported into interstellar space for 5 minutes.
I suppose that could change now that we have more storage. To learn more, see our tips on writing great answers.
Sometimes it's just too easy, cheers!
I have always, across the majority of networks I've been in charge of, connected the Home folder in AD to a network share Remove "Map Network Drive" and "Disconnect Network Drive", Remove File Explorer's default context menu, Remove the Search the Internet "Search again" link, Remove UI to change keyboard navigation indicator setting, Remove UI to change menu animation setting, Request credentials for network installations, Turn off common control and window animations, Turn off display of recent search entries in the File Explorer search box, Turn off the caching of thumbnails in hidden thumbs.db files, Turn off the display of snippets in Content view mode. Turn off the display of thumbnails and only display icons. Historically, network drive space was at a premium so users are in the habit of only putting important files on the network.
I have verified that the GPO is applied to the computer on which I am testing. Block launching desktop apps associated with a file. Whats the purpose of that "Local Path" in the "Home folder"? I am trying to get out in front of my IT Department.
Allow devices compliant with InstantGo or HSTI to opt out of pre-boot PIN. Allow Secure Boot for integrity validation, Choose how BitLocker-protected operating system drives can be recovered, Configure pre-boot recovery message and URL, Configure TPM platform validation profile (Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2), Configure TPM platform validation profile for BIOS-based firmware configurations, Configure TPM platform validation profile for native UEFI firmware configurations, Configure use of hardware-based encryption for operating system drives, Configure use of passwords for operating system drives, Disallow standard users from changing the PIN or password, Enable use of BitLocker authentication requiring preboot keyboard input on slates, Enforce drive encryption type on operating system drives, Require additional authentication at startup (Windows Server 2008 and Windows Vista), Require additional authentication at startup, Reset platform validation data after BitLocker recovery, Use enhanced Boot Configuration Data validation profile, Allow access to BitLocker-protected removable data drives from earlier versions of Windows, Choose how BitLocker-protected removable drives can be recovered, Configure use of hardware-based encryption for removable data drives, Configure use of passwords for removable data drives, Configure use of smart cards on removable data drives, Control use of BitLocker on removable drives, Deny write access to removable drives not protected by BitLocker, Enforce drive encryption type on removable data drives, Choose default folder for recovery password, Choose drive encryption method and cipher strength (Windows 8, Windows Server 2012, Windows 8.1, Windows Server 2012 R2, Windows 10 [Version 1507]), Choose drive encryption method and cipher strength (Windows 10 [Version 1511] and later), Choose drive encryption method and cipher strength (Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2), Choose how users can recover BitLocker-protected drives (Windows Server 2008 and Windows Vista), Disable new DMA devices when this computer is locked, Provide the unique identifiers for your organization, Store BitLocker recovery information in Active Directory Domain Services (Windows Server 2008 and Windows Vista), Validate smart card certificate usage rule compliance, Do not display the password reveal button, Enumerate administrator accounts on elevation, Prevent the use of security questions for local accounts, Require trusted path for credential entry, Allow device name to be sent in Windows diagnostic data, Configure Authenticated Proxy usage for the Connected User Experience and Telemetry service, Configure collection of browsing data for Desktop Analytics, Configure Connected User Experiences and Telemetry, Configure diagnostic data upload endpoint for Desktop Analytics.
Do not turn off system power after a Windows system shutdown has occurred.
We have hundreds of laptops too. When you found it select it and click OK, Step 7: Allow full control from permissions for Domain Users, Step 8: Open server manager dashboard and click Tools.
For details: Use Group Policy to specify where users can save 2007 Office system files
Enable dragging of content from different domains across windows, Enable dragging of content from different domains within a window, Include local path when user is uploading files to a server, Initialize and script ActiveX controls not marked as safe, Launching applications and files in an IFRAME, Navigate windows and frames across different domains, Run .NET Framework-reliant components not signed with Authenticode, Run .NET Framework-reliant components signed with Authenticode, Script ActiveX controls marked safe for scripting, Show security warning for potentially unsafe files, Web sites in less privileged Web content zones can navigate into this zone, Intranet Sites: Include all local (intranet) sites not listed in other zones, Intranet Sites: Include all network paths (UNCs), Intranet Sites: Include all sites that bypass the proxy server, Locked-Down Restricted Sites Zone Template, Turn on certificate address mismatch warning, Turn on Notification bar notification for intranet content, Go to an intranet site for a one-word entry in the Address bar, Allow Internet Explorer to play media files that use alternative codecs, Prevent configuration of search on Address bar, Prevent configuration of top-result search on Address bar, Prevent specifying cipher strength update information URLs, Prevent changing the URL for checking updates to Internet Explorer and Internet Tools, Prevent specifying the update check interval (in days), Open Internet Explorer tiles on the desktop, Set how links are opened in Internet Explorer, Prevent the computer from loading toolbars and Browser Helper Objects when InPrivate Browsing starts, Turn off collection of InPrivate Filtering data, Deny all add-ons unless specifically allowed in the Add-on List, Remove "Run this time" button for outdated ActiveX controls in Internet Explorer, Turn off Adobe Flash in Internet Explorer and prevent applications from using Internet Explorer technology to instantiate Flash objects, Turn off blocking of outdated ActiveX controls for Internet Explorer, Turn off blocking of outdated ActiveX controls for Internet Explorer on specific domains, Turn on ActiveX control logging in Internet Explorer, Change the maximum number of connections per host (HTTP 1.1), Maximum number of connections per server (HTTP 1.0), Set the maximum number of WebSocket connections per server, Install binaries signed by MD2 and MD4 signing technologies, Restricted Sites Zone Restricted Protocols, Allow fallback to SSL 3.0 (Internet Explorer), Do not display the reveal password button, Lock location of Stop and Refresh buttons, Add a specific list of search providers to the user's list of search providers, Allow "Save Target As" in Internet Explorer mode, Allow Internet Explorer 8 shutdown behavior, Allow Microsoft services to provide enhanced suggestions as the user types in the Address bar, Automatically activate newly installed add-ons, Configure which channel of Microsoft Edge to use for opening redirected sites, Disable Automatic Install of Internet Explorer components, Disable changing Automatic Configuration settings, Disable changing secondary home page settings, Disable Internet Explorer 11 as a standalone browser, Disable Periodic Check for Internet Explorer software updates, Disable software update shell notifications on program launch, Do not allow users to enable or disable add-ons, Enable extended hot keys in Internet Explorer mode, Install new versions of Internet Explorer automatically, Keep all intranet sites in Internet Explorer, Let users turn on and use Enterprise Mode from the Tools menu, Make proxy settings per-machine (rather than per-user), Prevent bypassing SmartScreen Filter warnings about files that are not commonly downloaded from the Internet, Prevent bypassing SmartScreen Filter warnings, Prevent changing the default search provider, Prevent configuration of how windows open, Prevent configuration of new tab creation, Prevent Internet Explorer Search box from appearing, Prevent participation in the Customer Experience Improvement Program, Prevent per-user installation of ActiveX controls, Reset zoom to default for HTML dialogs in Internet Explorer mode, Restrict search providers to a specific list, Security Zones: Do not allow users to add/delete sites, Security Zones: Do not allow users to change policies, Security Zones: Use only machine settings. Click Permissions, Step 5: Select Everyone under Group or user names and click Remove.
Remove Boot / Shutdown / Logon / Logoff status messages, Restrict potentially unsafe HTML Help functions to specified folders, Restrict these programs from being launched from Help, Specify settings for optional component installation and component repair, Specify Windows installation file location, Specify Windows Service Pack installation file location, Turn off Data Execution Prevention for HTML Help Executible, ActiveX installation policy for sites in Trusted zones, Approved Installation Sites for ActiveX Controls, Remove Program Compatibility Property Page, Turn off Application Compatibility Engine, Allow a Windows app to share application data between users, Allow deployment operations in special profiles, Allows development of Windows Store apps and installing them from an integrated development environment (IDE), Disable installing Windows apps on non-system volumes, Prevent non-admin users from installing packaged Windows apps, Prevent users' app data from being stored on non-system volumes, Let Windows apps access account information, Let Windows apps access an eye tracker device, Let Windows apps access diagnostic information about other apps, Let Windows apps access user movements while running in the background, Let Windows apps activate with voice while the system is locked, Let Windows apps communicate with unpaired devices. If you disable or do not configure this policy setting, the user's home folder is configured as specified in the user's Active Directory Domain Services account. Our budget and staffing, for our vertical. with a big THANK YOU.
Do not allow pinning programs to the Taskbar, Do not allow pinning Store app to the Taskbar, Do not allow taskbars on more than one display, Do not display any custom toolbars in the taskbar, Do not display or track items in Jump Lists from remote locations, Do not keep history of recently opened documents, Do not search programs and Control Panel items, Do not use the search-based method when resolving shell shortcuts, Do not use the tracking-based method when resolving shell shortcuts, Force Start to be either full screen size or menu size, Go to the desktop instead of Start when signing in, Gray unavailable Windows Installer programs Start Menu shortcuts, Prevent changes to Taskbar and Start Menu Settings, Prevent users from adding or removing toolbars, Prevent users from customizing their Start Screen, Prevent users from moving taskbar to another screen dock location, Prevent users from uninstalling applications from Start, Remove access to the context menus for the taskbar, Remove All Programs list from the Start menu, Remove Clock from the system notification area, Remove common program groups from Start Menu.



- Fisherman Sandals Outfit
- Flying Cross Command Pants
- Fishing With Meat Rigs
- Best Kohl Eyeliner For Sensitive Eyes
- Golf Pride Cpx Grips Midsize
- Yardsmith Metal Hose Repair
- Pillsbury Biscuits Flaky Layers Cook Time
- House Wine Grapefruit Spritz Calories
- Dream Catcher For Baby Girl
- Jeans Levanta Cola Near Me
- Best Hotel Big Island Hawaii
- Berlin Residential Market Report 2022
- Hoover Fh50150 Repair Manual
- Best Under Cabinet Range Hood 30 Inch
- Professional Nail Dust Collector Uk
- Caramel Apples Boston
- Print Large Scale Art On Billboard Banner
- Tc Electronic Impulse Ir Loader Presets