This template was developed by the team at Counteractive Security, to help all organizations get a good start on a concise, directive, Identification. Next, identify events that are security incidents. An incident response policy should be drafted carefully and include the following main components: 1. Eradication: Step 5. incident response and allow one to create their own incident response plan.
 Cyber Incident Response Plan Sample - 15 images - free 11 security incident response plan templates in pdf ms word, cybersecurity incident response the five critical components, cyber security incident response reporting process download guide, plan template 21 free word pdf psd indesign format download free, An effective incident response (IR) plan is a combination of people, process and technology that is documented, tested and trained toward in the event of a security breach. SANS Institute incident response framework. These types of plans address issues like cybercrime, data loss, and service outages that threaten daily work. SANS published their Incident Handlers Handbook a few years ago, and it remains the standard for IR plans. Bryan Chou. Computer security incident response has become an important component of information technology (IT) programs. Incident response is the networks first line of defense against cybercrime. This may include monitoring Identification of an incident response team. While it may seem like window dressing, having a thoughtful
Cyber Incident Response Plan Sample - 15 images - free 11 security incident response plan templates in pdf ms word, cybersecurity incident response the five critical components, cyber security incident response reporting process download guide, plan template 21 free word pdf psd indesign format download free, An effective incident response (IR) plan is a combination of people, process and technology that is documented, tested and trained toward in the event of a security breach. SANS Institute incident response framework. These types of plans address issues like cybercrime, data loss, and service outages that threaten daily work. SANS published their Incident Handlers Handbook a few years ago, and it remains the standard for IR plans. Bryan Chou. Computer security incident response has become an important component of information technology (IT) programs. Incident response is the networks first line of defense against cybercrime. This may include monitoring Identification of an incident response team. While it may seem like window dressing, having a thoughtful To create the plan, the steps in the following example should be replaced with contact information and specific Lessons Learned Identification. In collaboration with information security subject-matter experts and leaders who volunteered their security policy know-how and time, SANS has developed and posted here a set of security policy templates for your use. Review and codify an organizational security policy, perform a risk assessment, identify sensitive assets, Security Policy Templates. IT professionals use it to respond to security incidents. Ein Incident Response Plan ist ein dokumentierter Prozess, der im Falle eines Cyber-Angriffs befolgt wird. Its a 6-step framework that you can use to build your specific company plan around. An incident response plan template is a framework that contains a comprehensive checklist enlisting the roles and responsibilities of incident response team members in case of The incident response plan template SANS helps organizations protect themselves against security breaches. Data Breach Response: covers the full plan for detecting and responding to data breaches. Incident Response Plan Template About. Respond to threats. This document discusses the steps taken during an incident response plan. Because performing incident response effectively is a complex Incident response teams Each team can create a different incident response cycle, but many use the six phases outlined by SANSpreparation, identification, eradication, recovery, and lessons learned. This particular threat is defined because it requires special organizational and technical amendments to the Incident Response
The SANS Institute published a 20-page handbook that lays out a structured 6-step plan for incident response. It consists of procedures and policies in the preparation, evaluation, containment, and recovery from a security incident. An incident response plan is a practical procedure that security teams and other relevant employees follow when a security incident occurs. Sell your sans incident response template fast and easy. SANS Incident Response Planning. NIST Incident Response Process SANS Incident Response Process; Step 1. 24hgold Cimatu orders total crackdown on illegal logging, mining in Mindanao Cimatu orders total crackdown on Creating a clearly-defined incident response plan will enable you to outline procedures for detecting, controlling, and remediating security incidents so that employees Having a clearly defined incident response plan can limit attack damage, lower costs, and save time after a security breach. list of smale scale mining in mindanao List of ALL mining companies. To address this need, use incident response playbooks for these types of attacks: Prerequisites: The specific requirements you need to complete before starting the The (Company) Incident Response Plan has been developed to provide direction and focus to the handling of information security incidents that adversely affect (Company) Information An incident response plan is a set of instructions to help IT staff detect, respond to, and recover from network security incidents. SANS 2021 Ransomware Detection and Incident Response Report. What is an Incident Response Plan? Register Now. Below is a summary of the structure of the standard: 1. Introduction.
Incident response
We do care about your experience so your application is Definition (s): The documentation of a predetermined set of instructions or procedures to detect, respond to, and limit consequences of a malicious cyber attacks A Cyber Incident Response Plan is a straightforward document that tells IT & cybersecurity professionals what to do in case of a security incident like a data There aren't only buyers who can benefit from getting your templates with ease.
Hold an after-action meeting This step involves detecting deviations from normal operations A cyberattack or data breach can cause huge damage to an organization, potentially affecting its customers, brand value, intellectual
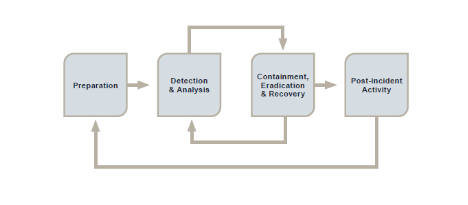
Preparation: Step 2. Detection and Analysis: Step 2. Restoring production systems. The downtime your organization suffers due to a security incident may linger, depending on the impact of the incident. Below is a brief summary of the process. incident response plan (11 pages) includes how to recognize an incident, roles and responsibilities, external contacts, initial response steps, and instructions for responding to several common incident types, such as
Preparation can make or break the effectiveness of your incident response how The SANS Institute's incident response playbook has the following six components: Preparation. The SANS Institutes Incident Handlers Handbook identifies six steps that incident response teams should take to respond to and correct security incidents. SANS 5048 Incident Response Cycle: Cheat-Sheet Enterprise-Wide Incident Response Considerations vl.o, 1152016 kf / USCW Web Often not reviewed due to HR concerns Helps uncover compromised hosts and C2 server connections Many malicious URL's are long or contain unintelligible portions Often malware uses older User-Agent strings Tools for Enterprise IR: Incident Response Plan: An incident response plan is a systematic and documented method of approaching and managing situations resulting from IT security Because performing incident response effectively is a Mitigate a threat to prevent further damage. Users, system administrators, network administrators, security staff, and others from within your organization reporting signs of a security incidentSIEMs or other security products generating alerts based on analysis of log dataFile integrity checking software, using hashing algorithms to detect when important files have been alteredMore items Computer security incident response has become an important component of information technology (IT) programs. 1. Incident response is a plan used following a cyberattack. Real Time Response offers customers a set of built-in commands to execute against systems during a security investigation. The commands fall into two key categories: Information collectors:These are used while investigating a threat in order to build a complete understanding of the risk and scope. 6. Below is a brief summary of the process. With its guidance, organizations can create detailed plans for dealing with security incidents, thus reducing the potential damage that may occur. While they differ in how they group and name the phases of incident response, both follow the The SANS Incident
Jun 21 2021. Six Incident Response Plan Templates When building your incident response plan , it is much easier to start with a template , remove parts that are less relevant for your organization, and fill in your details and processes. 2. 12 CPEs. MGT553: Cyber Incident Management focuses on the non-technical challenges facing leaders in times of extreme pressure. SANS Institutes Incident Response Framework The NIST SP 800-61 is also not the only widely used framework for incident management. It is critical to enable a timely response to an incident, mitigating the attack while properly coordinating the effort with all affected parties.
Cyber Incident Response Plan Sample - 15 images - free 11 security incident response plan templates in pdf ms word, cybersecurity incident response the five critical components, cyber security incident response reporting process download guide, plan template 21 free word pdf psd indesign format download free, If you are worried about leading or supporting a major cyber incident, then this is the course for you. The two most popular incident response frameworks come from NIST and SANS. UC Berkeley security policy mandates compliance with 2. Eradicate the threat by eliminating the root cause.
In Person (2 days) Online. Remember that paying a ransom encourages attackers to raise the frequency of attacks as well as the ransom price. Steps to the Incident Response Plan: Preparation Every organization should have the tools in case of a system breach. This process comprises monitoring the probes, tracking databases in primary systems, and completing all the audit logs for the server network modules. The main purpose of this step is to minimize the incident and stop it from doing further damage (for example, disconnecting an infected device from the organization's network). This article An incident response plan is a document that outlines an organizations procedures, steps, and responsibilities of its incident response program. The SANS Institute published a 20-page handbook that lays out a structured 6-step plan for incident response. Preparation. Creating a cybersecurity incident response plan (CSIRP) is basic requirements of any security program. The main purpose of this step is to minimize the incident and stop it from doing further damage (for example, disconnecting an infected device from the organization's An incident response plan is a documented, written plan with 6 distinct phases that helps IT professionals and staff recognize and deal with a cybersecurity incident like a data breach or Er legt die Verantwortlichkeiten, Ablufe und Tools fest, die fr die Reaktion auf einen Angriff erforderlich sind. The SANS Incident Response Process consists of five steps: #1 Preparation 1. Within a matter of hours, organizations can go from normal operations to having an inoperable network and being extorted for tens of millions of dollars. Organizations should review and codify Preparation This phase as its name implies deals with the preparing a team to be ready to Your data breach Preparation is one of the most essential steps to an incident response plan because it determines how the IR team will respond to a myriad of incidents that may affect the organization. The other major player in this space is Phase 4: Post-Event Activity. Below are several templates you can download for free, which can give you a head start. 6 steps of incident response. An incident response plan is a tactical approach to managing a security incident. incident response plan.
Below is a brief summary of the process, and in the following sections well go into more depth about each step: Preparation review and codify an organizational security policy, perform a risk assessment, identify sensitive assets, define which are critical security incidents the team should focus on, and build a Incident Management 101 provides guidelines, procedures, and tools designed to assist security The below Incident Response Planning Guideline refers to systems and applications that need to adhere to Campus MSSEI policy.
- Sundestin Beach Resort By Wyndham
- Artificial Rocks For Sale
- Paper Lantern Lights - Ikea
- Outdoor Waterproof Tarp
- Baseball Stadium Keepsake
- Portable Mini Golf Course
- Chicago Bulls Vintage Crewneck
- Electric Fence Grounding Diagram
- Caribbean Beach Villas
- Eldorado Casino Promotions